Sws101_unit1
Topics : Networking.
Before knowing about networking.
Before knowing about networking, I had a basic understanding of the Internet that it’s just a radio signal transmitting from the device to satellite and bouncing back to it. More over I thought that WIFI and hotspot it’s a local network that acts like a internet. on top of that the surprising thing was sharing hotsport from mobile to computer/laptop because I didn’t even thought that we could use internet on laptop from phone. 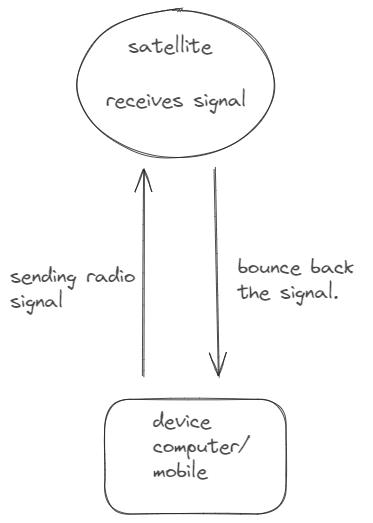
Not only but also the confusing part is that when we use hostport from phone, like I have mentioned above phone acts like a satellite. What ever the computer is requesting it gets using the internet from the phone.
After learning about networking.
How does the internet work? The web broswer connects to the web server and send a http request for the web page. When the web server recevices the requested page. It check for the requested page and sends back the page. If the desired page is not found then the web server will send the http 404 error which means that the page is not found in the server. 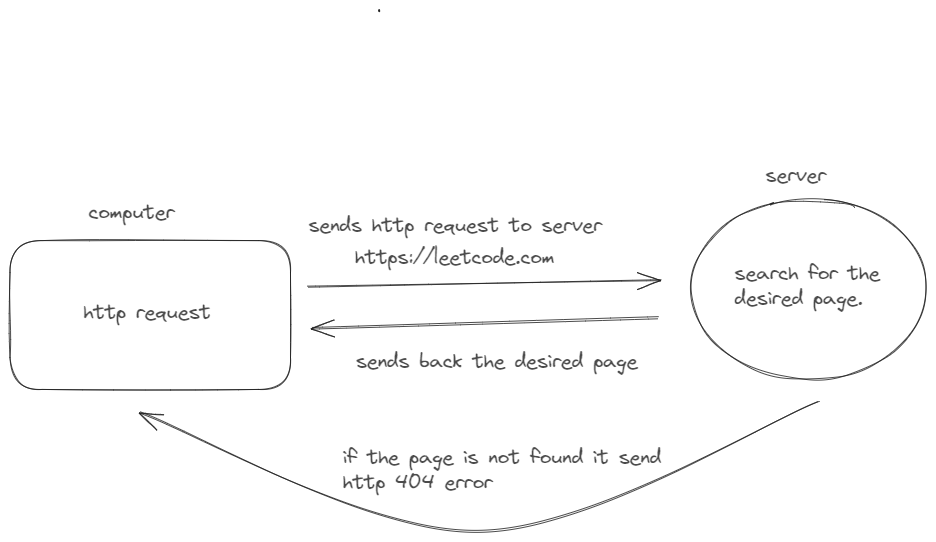
How does computer network work? Computer uses a system of rules called communication protocols to transmit information over physical or wireless technology.
Topics: Bandit game
Level 0. In level 0 I have log into the game server using ssh(secure shell protocol) on port 2220 and password is bandit0. In level0 the password for next level is stored in file called readme. I used ls to see the file and used cat command to see the content of the file. So I got the password for the next level. 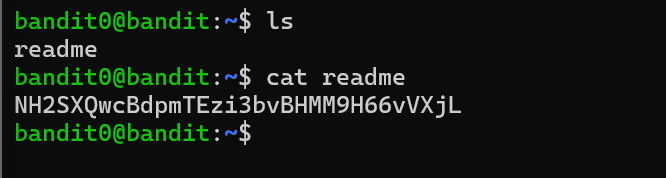
Level 1 I used the ls to see what files are there in the directory. There I found a file called - in the home directory and used cat < - to see the content of the file. 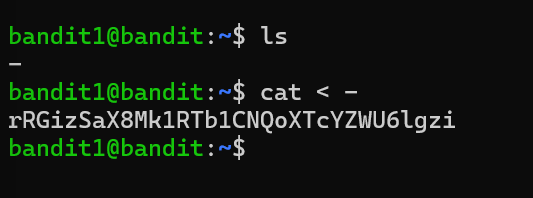
Level 2 the file in this level is stored in the file named spaces in the filename in home directory. So I used cat “spaces in the filename” and found the password.
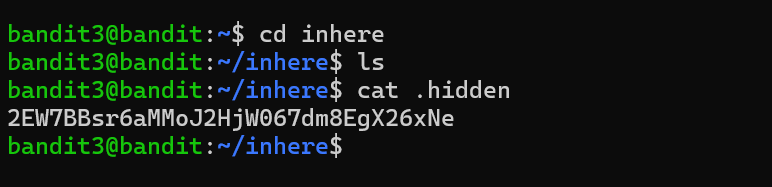
Level 3 the file in this level is hidden in inhere directory. I changed the file directory to inhere and ls to see the files. So I used cat .hidden command to see the hidden file.
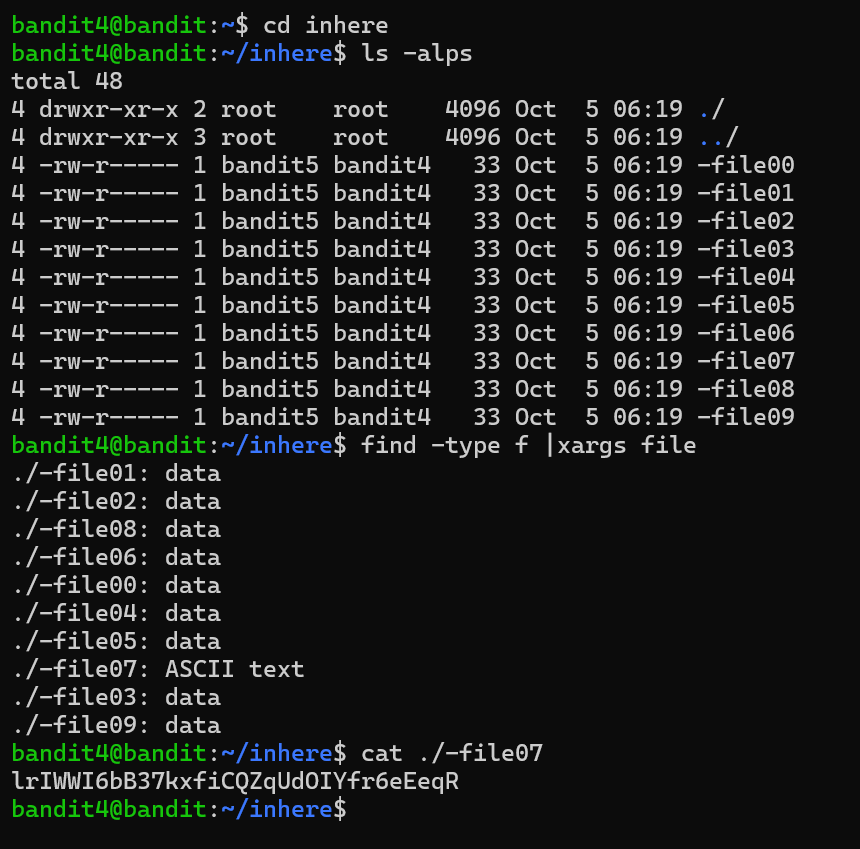
Level 4 the file is present in the inhere directory and it’s human readable. I changed to inhere directory and saw many files. There was a -file07 ACSII text thats human readable. So cat ./-file07 and got the password.
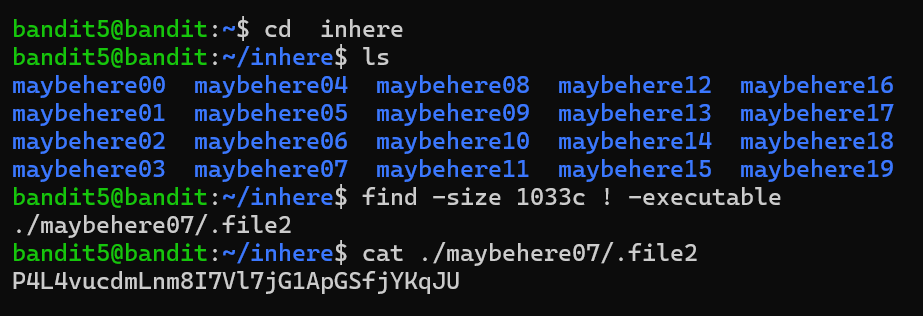
Level 5 the file is present in the inhere directory that’s human-readable, 1033bytes in size and not executable. changed the directory to inhere, ls the file and used the find -size 1033c ! -executable and cat ./maybehere07/.file2.
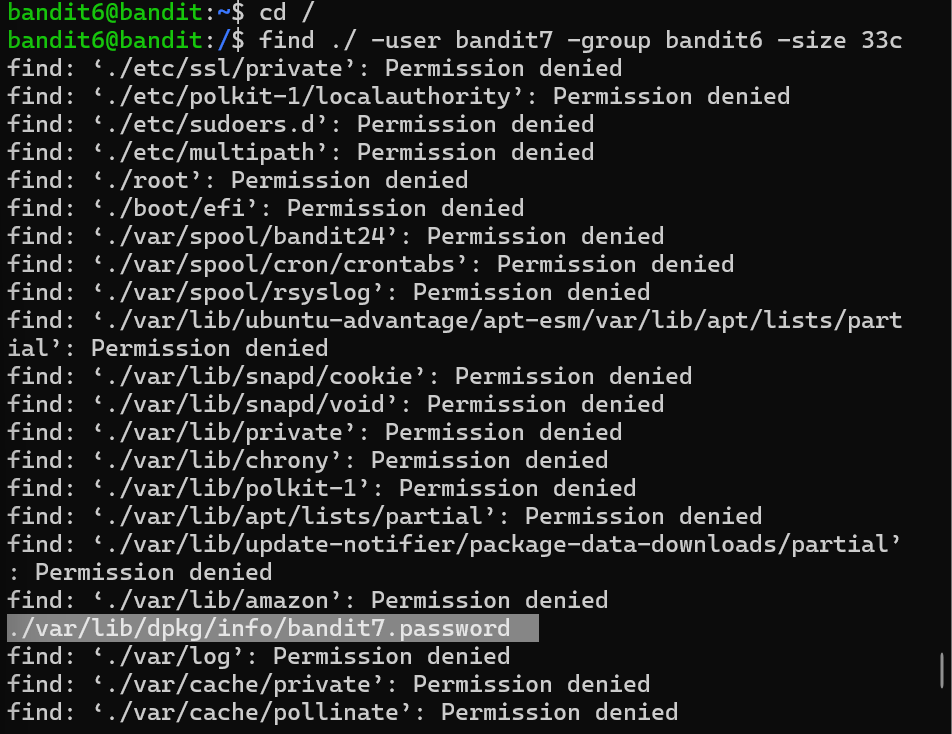
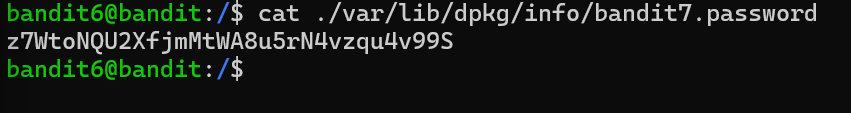
Level 6 the file is present in the server and some properties of the file was given username, user group and the size of the file. i use the find ./ -user bandit7 -group bandit6 -size 33c. It showed me the list of files. But the file ./var/lib/dpkg/info/bandit7.password was the file I wanted. So cat ./var/lib/dpkg/info/bandit7.password.
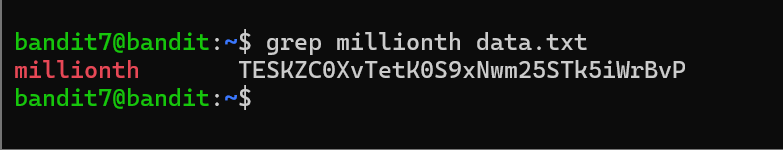
Level 7 the file is present next to the word millionth. I used grep millionth data.txt(grep command is used to search for lines matching the specific pattern) and the result was showed.
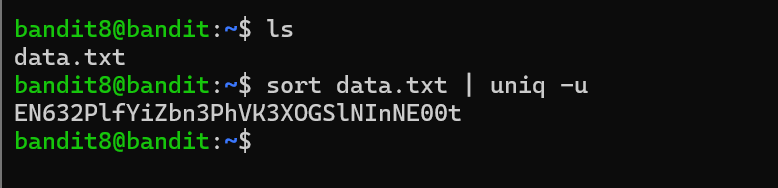
| Level 8 the file is present in a unique way so I used ls to list the files and sorted the files as specified **sort data.txt | uniq -u**. |
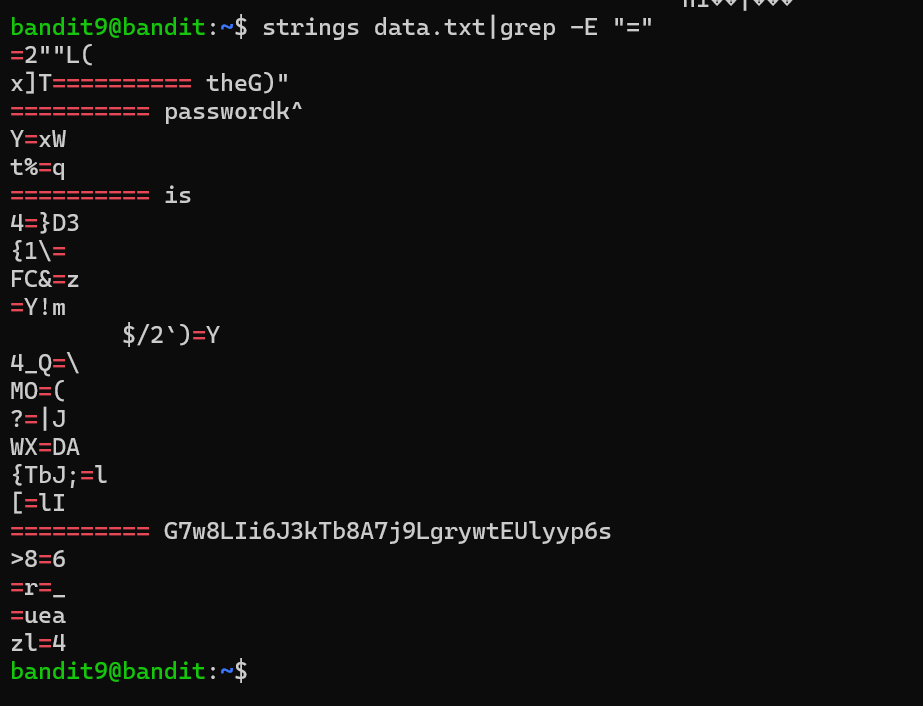
| Level 9 the file is present in a data.txt and it’s human readable strings. I ls the file list and found data.txt. I **sort data.txt | uniq -u**, it listed many files. So I used **strings data.txt | grep -E “=”**. |
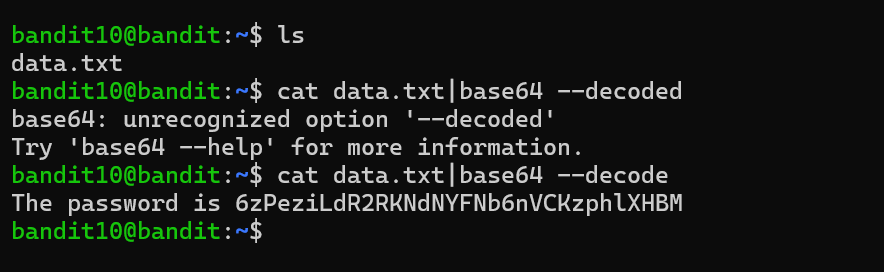
| Level 10 the file is present as base64 encoded data. I ls the file and found data.txt. So I used **cat data.txt | base64 –decode** and found the answer. |
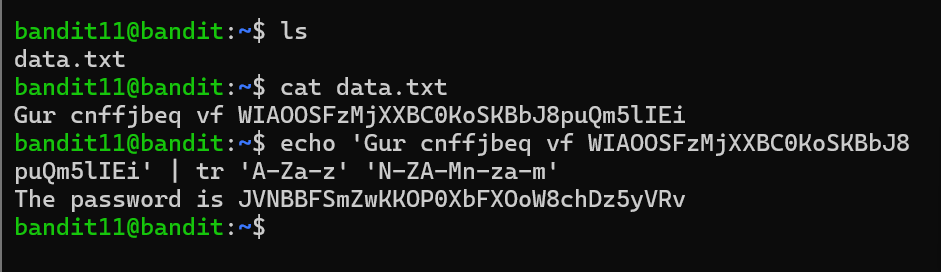
| Level 11 the file is present in data.txt where all lowercase (a-z) and uppercase (A-Z) letters have been rotated by 13 positions. I found there is data.txt in home home directory. I cat data.txt and found the Rot13 letters(a simple letter substitution cipher that replaces a letter with the 13th letter after it in the Latin alphabet). So I used **echo ‘Gur cnffjbeq vf WIAOOSFzMjXXBC0KoSKBbJ8puQm5lIEi’ | tr ‘A-Za-z’ ‘N-ZA-Mn-za-m’**. |
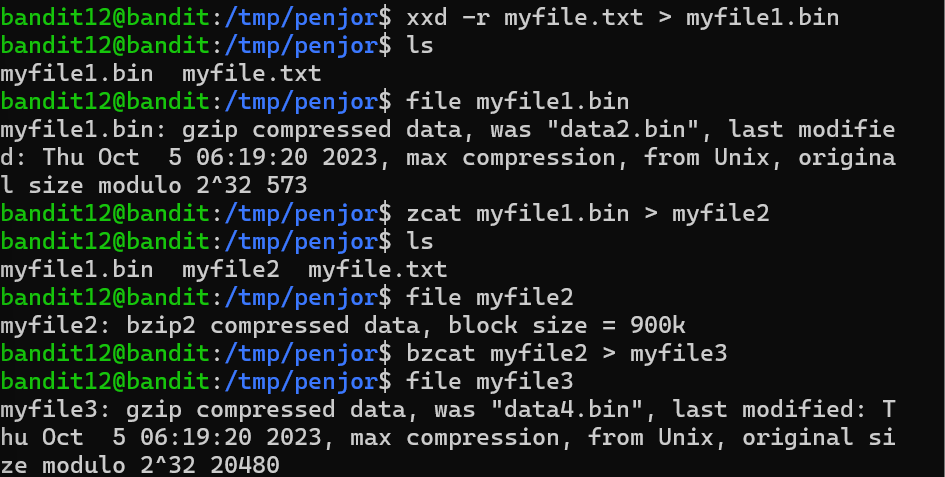
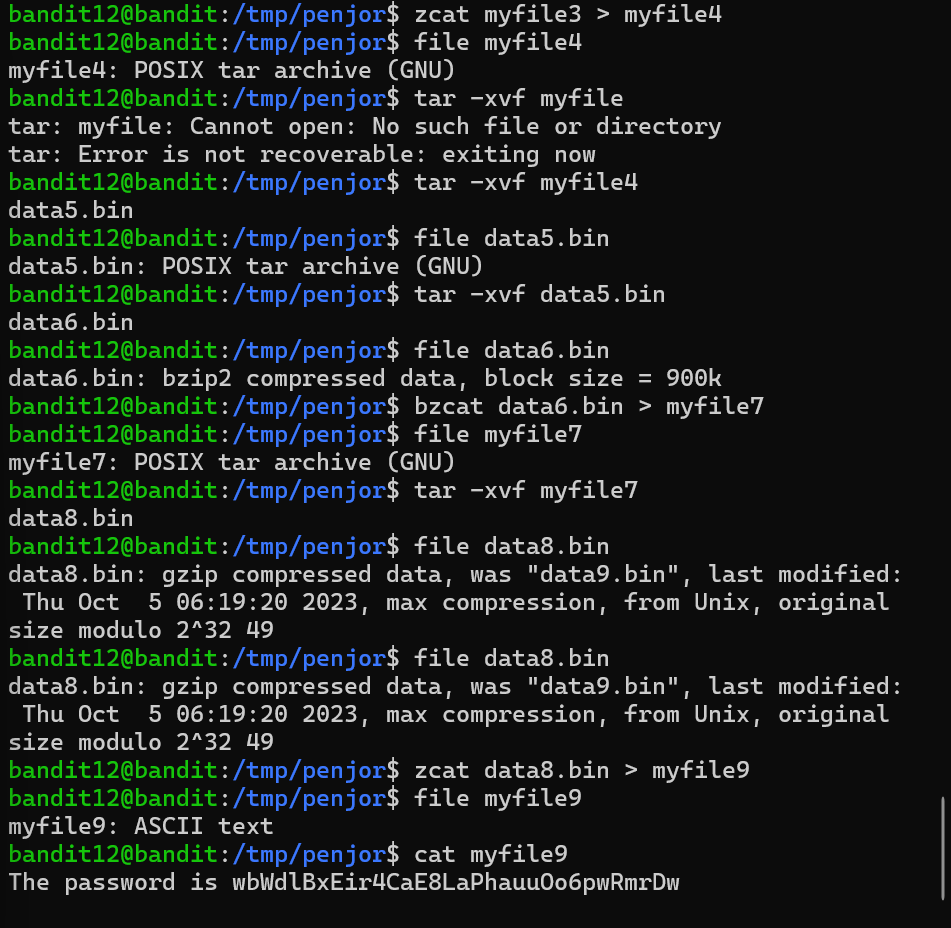
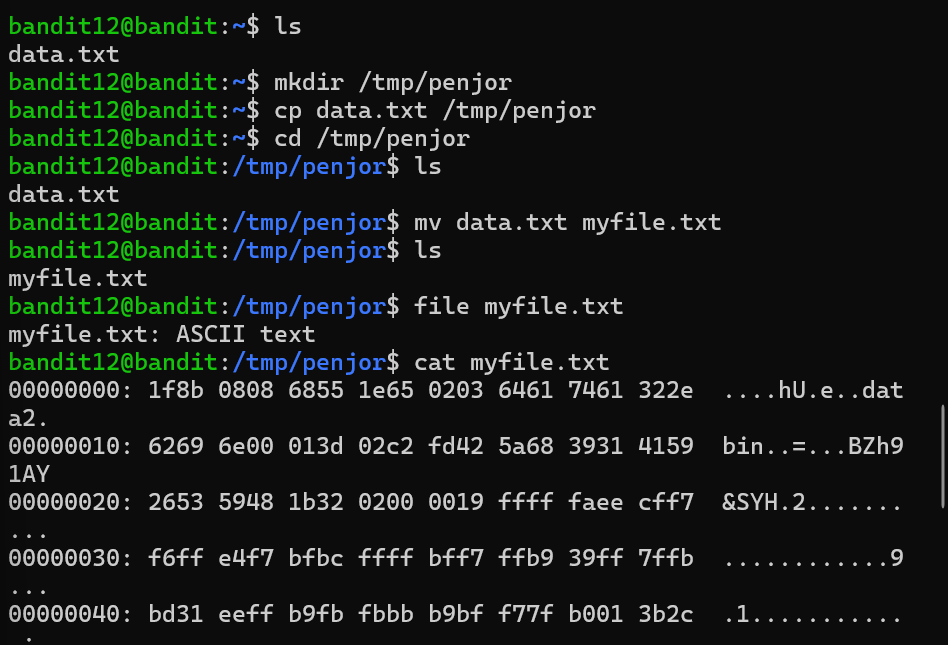
Level 12 the file is present in data.txt as hexdump( representation of a binary data stream where the contents of that stream are displayed as hexadecimal values.). I had create a folder /tmp/penjor and copied the file to folder I have created, I used mv to rename the file as myfile.txt. I used cat command to see the hexdump. After that I did repeated decompress till I get a readable text using xxd(creating and analyzing hexadump from files), zcat(allows the user to expand and view a compressed file without uncompressing that file), tar xvf(extracts files from an archive).
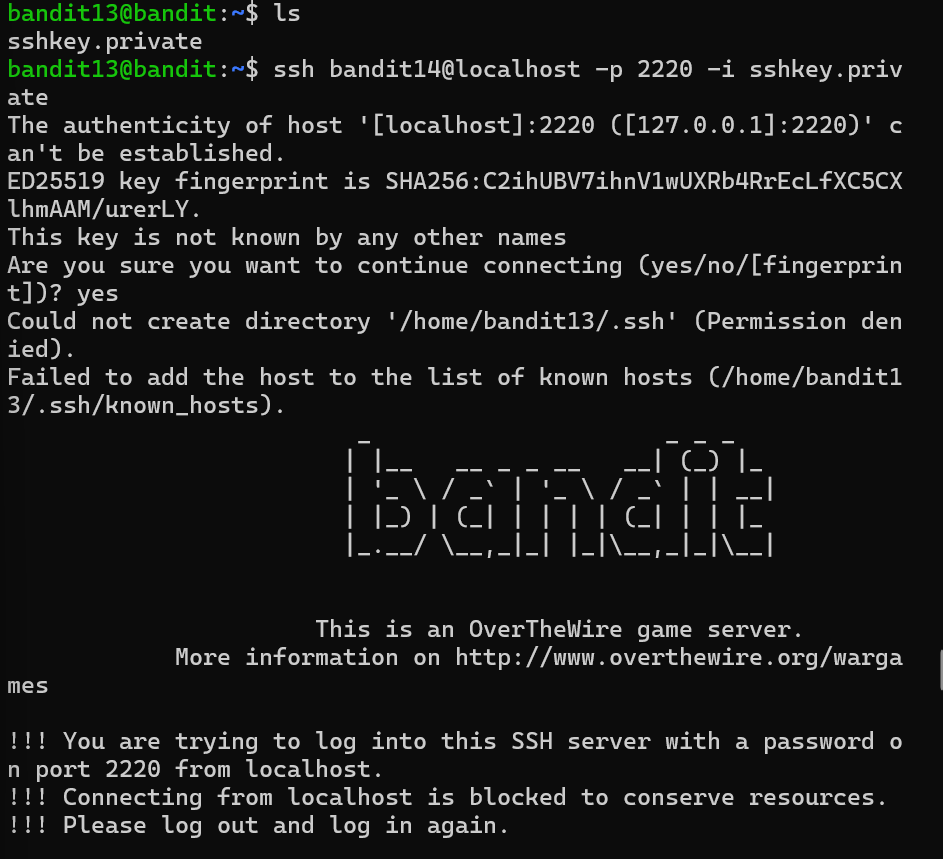
Level 13 in this level we will not get the password for next levelbut we are asked to login using sshkey.private, localhost as the hostname.
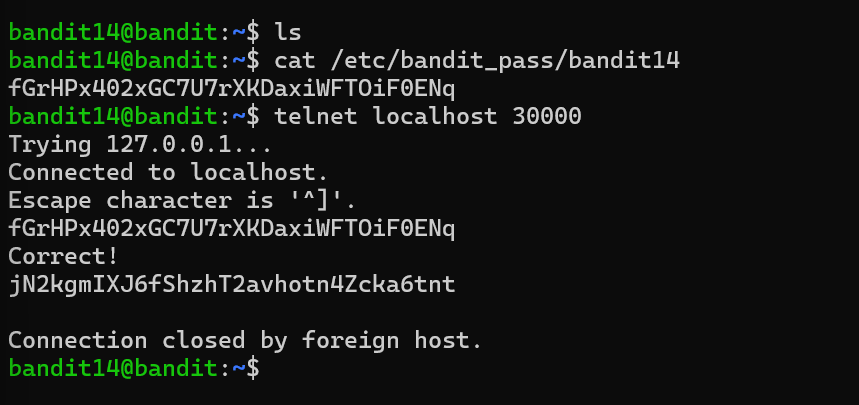
level 14 the sshkey is key to login into lecel 14. I submitted the password from /etc/bandit_pass/bandit14 to port 30000 telnet localhost 30000.
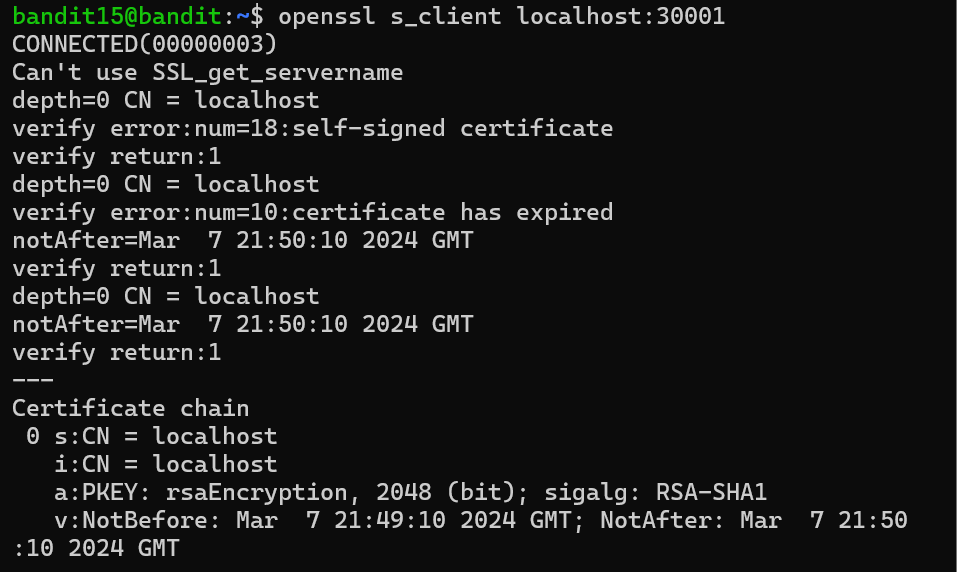
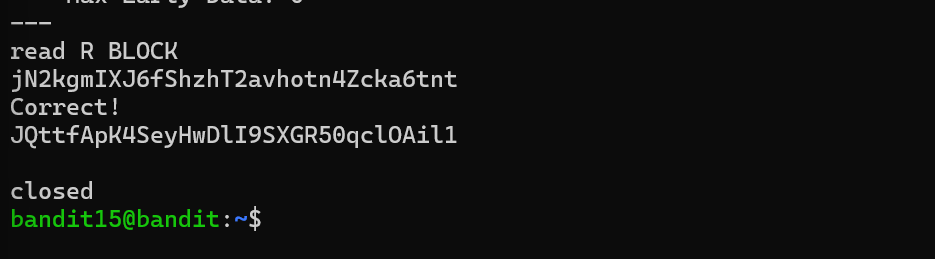
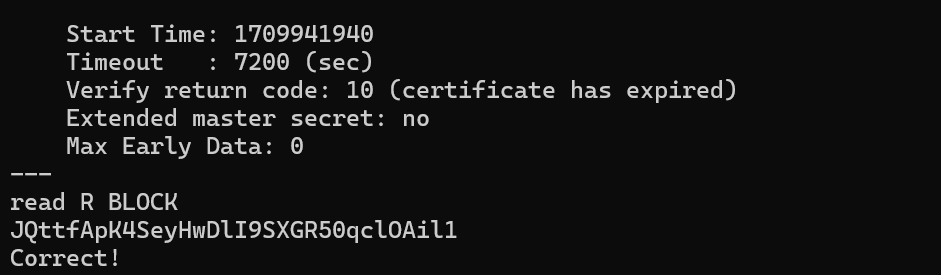
Level 15 I submittd the password from level 14 to port 30001 on localhost.I used openssl s_client localhost:30001.
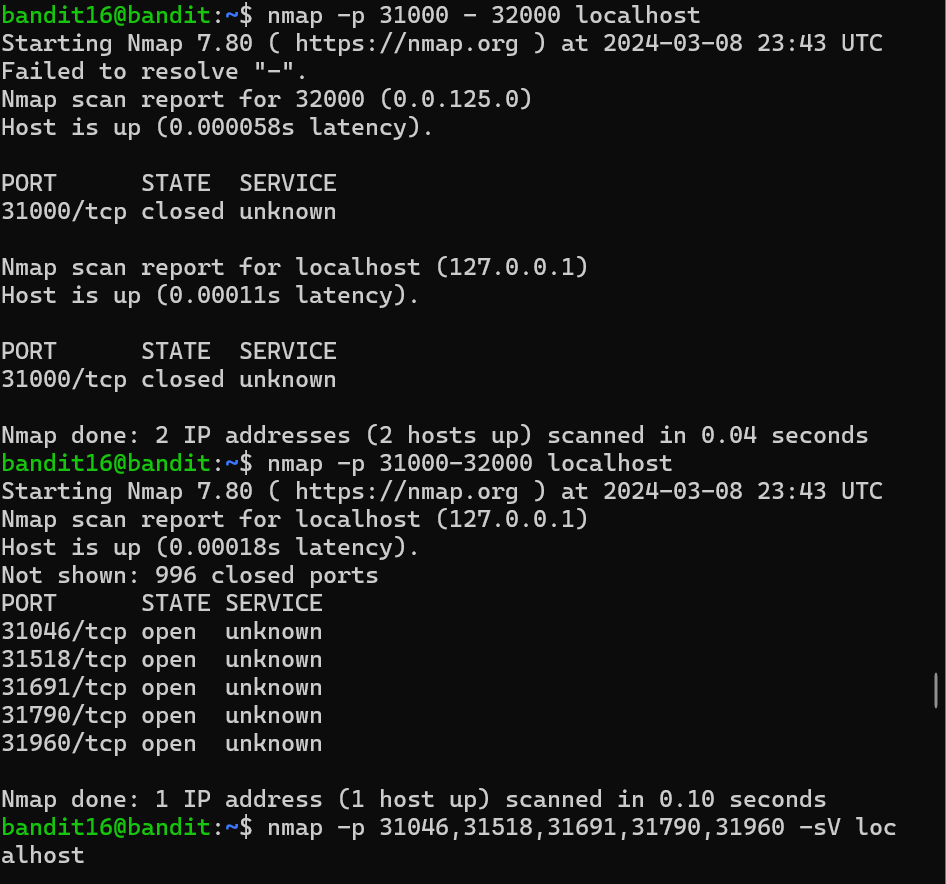
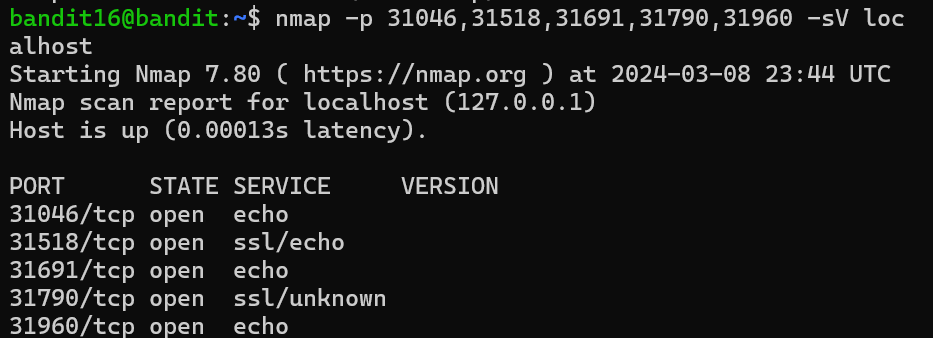
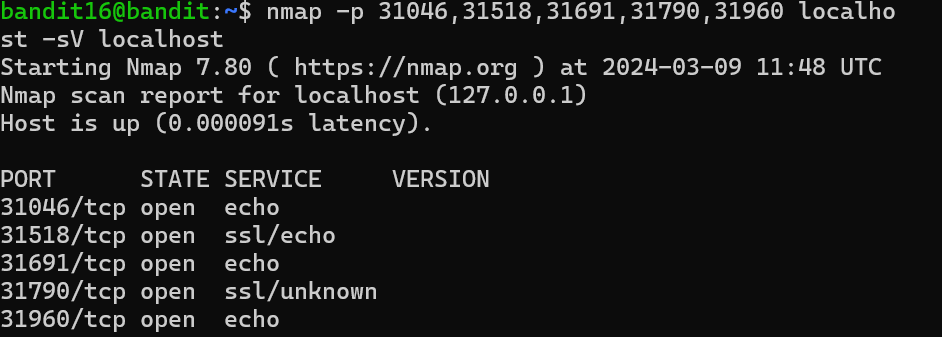
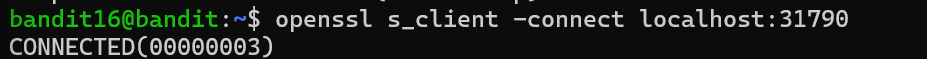
Level 16 in this level I have to see which port is online between 31000 to 32000.So the ones that runs SSL Encryption is my targe, using nmap -p 31000-32000 localhost. There were list of port shown, to see which port is listening I used nmap -p port list -sV localhost. It shows port 31790 and it is unknown. I passed the password to port 31790 using openssl s_client -connect localhost:31790. It showed me the correct password and gave me the RSA PRIVATE KEY.
Level 17 in this level there are two files in the home directory. I uses diff password.new passwords.old and showed the two password. From two password the 1st one worked got Byebye1 text.
Level 18 in level I was log out when i try login but the file is present in the readme in the home directory. So I used ssh bandit18@bandit.labs.overthewire.org -p 2220 ‘cat ~/readme’ and I got the password for the next level.
Level 19 in this level i used setuid binary (set user ID) after login it showed me bandit20-do. I used cat ./bandit20-do didn’t work and try for ./bandit20-do id. it works and found the password for next level.
Level 20 I list the file using ls and found the suconnect and used ls -al ./suconnect and found the file. I set up the TCP server that listen on port 61337. After that I excuted the setuid binary to the localhost on -p 61337 and found the password.